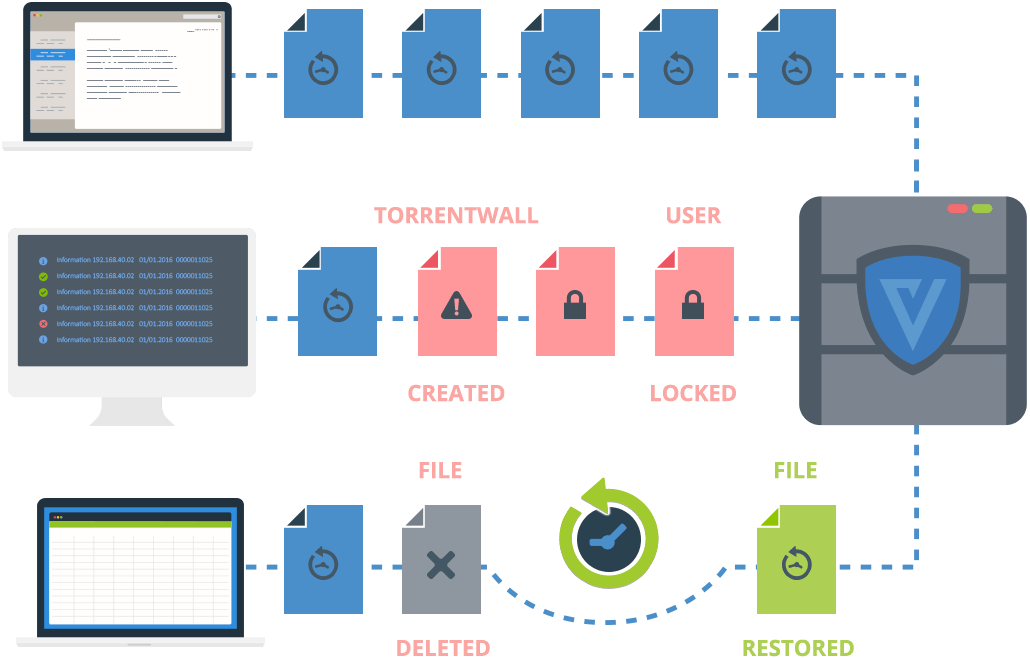
Veriato RansomSafe™ acts as a vital layer in your ransomware defense, combining just-in-time data protection with multiple mechanisms to detect, and shut down attacks before they hold your business hostage.

Protection
VShould ransomware reach your file server, Veriato RansomSafe™ detects the attack and shuts it down before your data is encrypted.

Fail-safe Backups
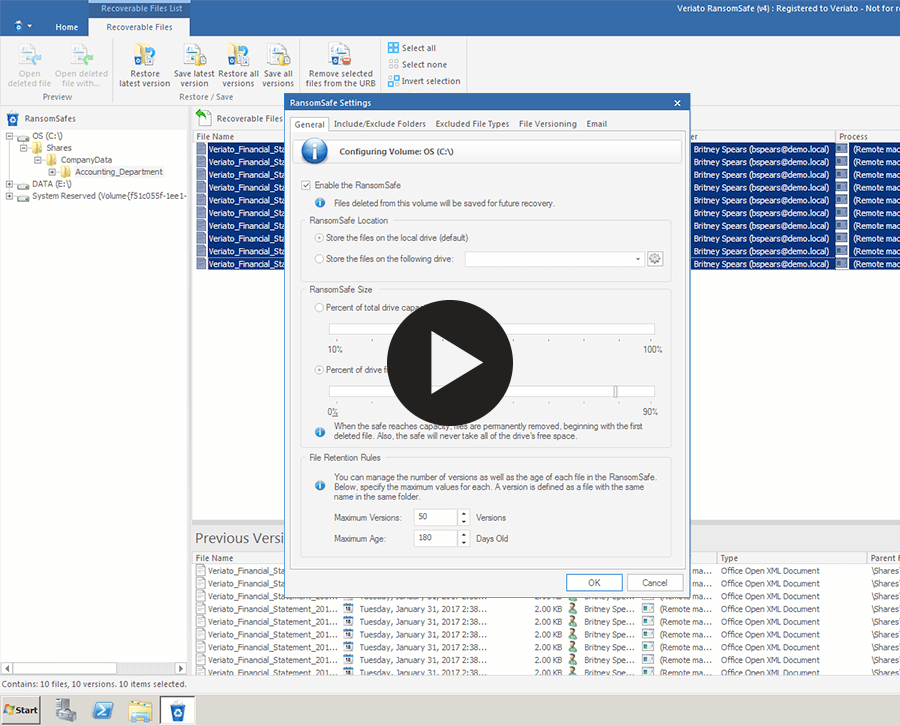
RansomSafe™ backs up your files before they are changed, making a pristine copy of the latest version of your files.

Rapid Recovery
Once the attack is disrupted, recover in minutes with just a few clicks. No extensive, and expensive, downtime.